Information Security Management


Information Security Management Framework
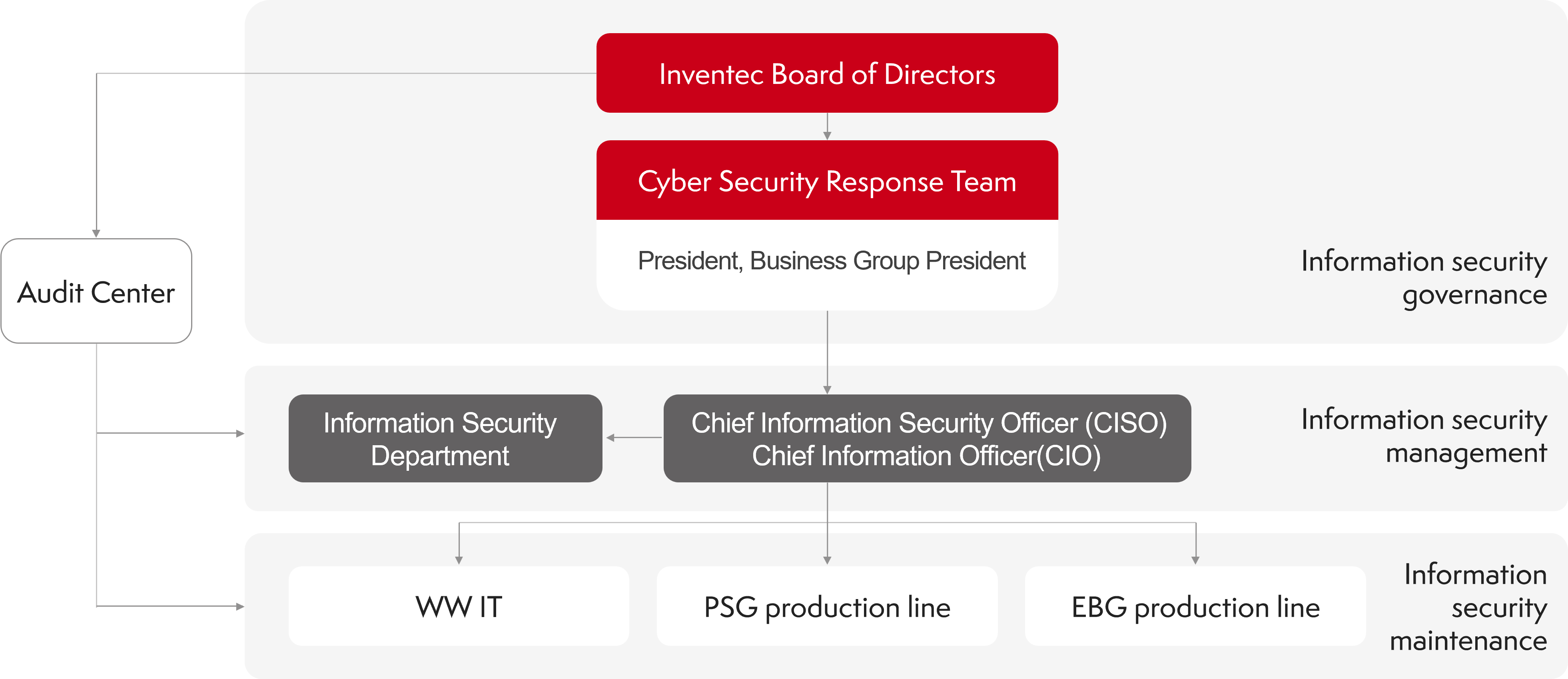
Information Security Organizational Structure
Inventec is led by the Chief Information Security Officer and is in charge of the information security management departments at the headquarters and each factory. The information security organization personnel are in charge as follows.
Chief Information Security Officer: Responsible for promoting information security policies and resource allocation, reporting to the President.
Head of Information Security Department at Headquarters:Responsible for planning and managing the group's information security system, reporting to the Chief Information Security Officer.
Staff in the Information Security Department at Headquarters: Responsible for the execution, protection and monitoring of the group's information security business.
Head of Information Security Department at Site: .Responsible for planning and managing the information security system at the site, reporting to the Chief Information Security Officer.
Staff in the Information Security Department at Site: Responsible for executing, protecting, and monitoring information security operations at the site.
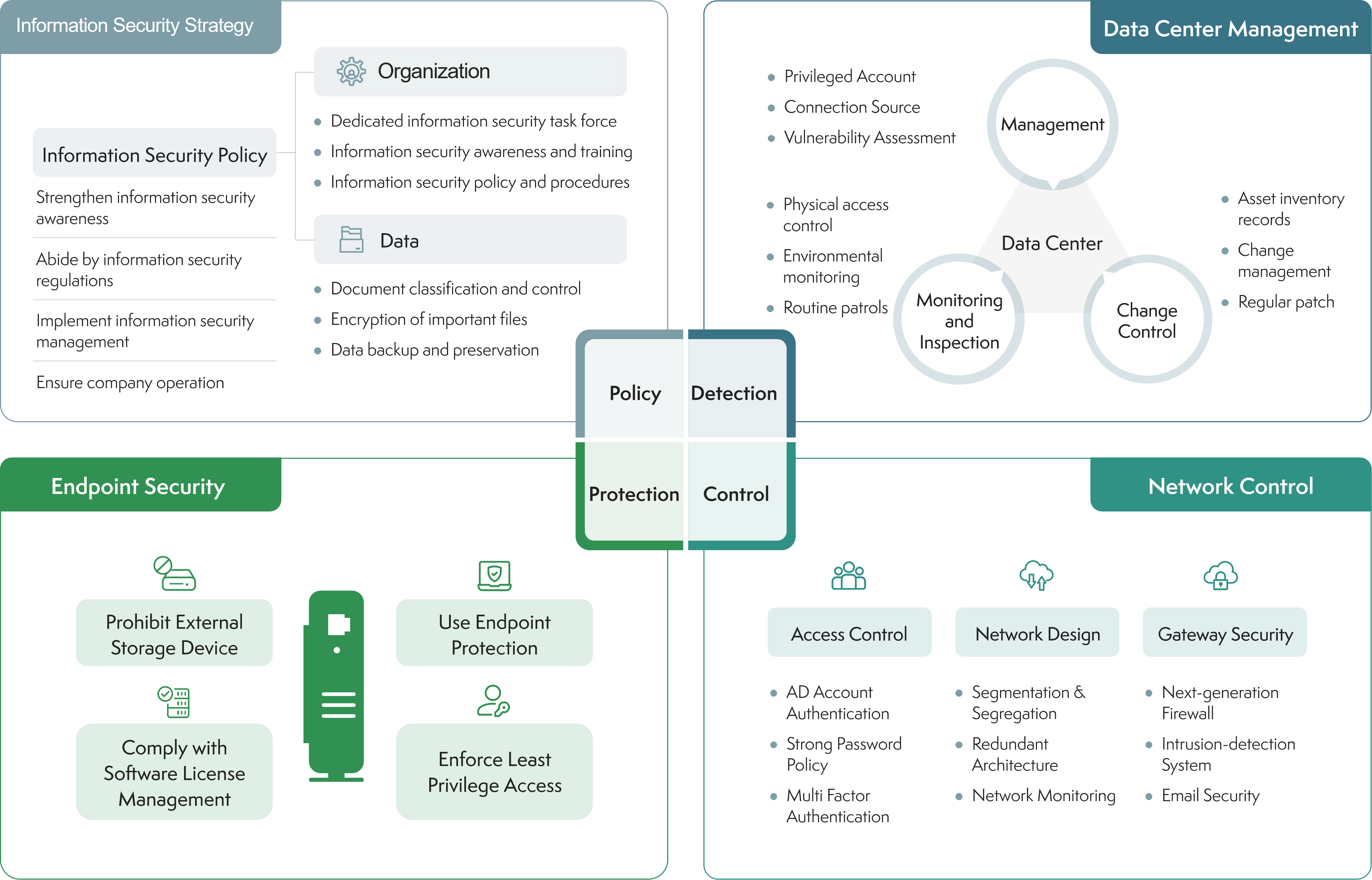
Information Security Management Measures
In accordance with ISO 27001 International Information Security Management Standards, Inventec has formulated its information security policy. Taking into account local regulations and business norms, each factory follows the information security policy and sets the goals to ensure customers’ requirements for information security are met.
Based on the information security goals, each unit carries out relevant management measures. The information security policy and suitability of the goals are reviewed annually to ensure that the company's system and network operations achieve confidentiality, integrity and accessibility.
Pursuant to the “Annual Internal Audit Plan” approved by the Board of Directors, Inventec conducts information security audit project on a regular basis to oversee the risk assessment and planning of the Information Security Management System (ISMS) as well as the implementation of the information security policy. The audit results will be reported to the Board of Directors.
Every year, all colleagues are required to sign the acknowledgement form of “Employee Code of Conduct”, which includes information security protection measures, and information security announcements are issued timely to remind employees to be vigilant about information security risks.
Information security training sessions are held regularly to update Inventec’s information security management regulations, cultivate a strong sense of information security among employees, and ensure full compliance with relevant information security regulations.
Information security education and training are conducted for general employees, providing them with the latest information security cases and popular information to improve their information security literacy.
Adoption of next-generation firewalls to reinforce the network boundary and safeguard against external threats.
Establishing a dual-layer defense architecture to effectively segment the network for production lines, client endpoints, and data center servers and enhance the depth of security protection.
Promoting Network Access Control (NAC) to manage access, identify internal devices and check their security compliance before connecting to the intranet.
Importing the bastion host or jump host to unify the host connection portal, reducing the risk of infiltration.
Establishing a document confidentiality classification system and strengthening the access control mechanism for personal data.
Using encryption software to protect confidential data and reduce the risk of leakage.
Performing system backups on a regular basis to minimize the cost of data loss.
Introducing an Advanced Persistent Threat (APT) protection scheme to enhance APT attack protection and monitoring, safeguarding Inventec’s information security against malware and hacker attacks.
Monitoring virus detection in all factories across the globe, carrying out necessary protective measures as well as virus containment management, tracking the cause of virus contact with computers in each area, and confirming that the viruses have been eradicated.
All computers within the domain are required to install antivirus software, with weekly antivirus scans scheduled.
Remote connections require two-factor authentication, and computer connections within the domain are restricted.
Email protection mechanism is activated to filter out malicious attachments and phishing links, preventing social engineering attacks by hackers.
Employees are required to use legitimate software to avoid causing harm to the company.
Performing data backups and restoration drills on a regularly basis to validate the effectiveness of the backup mechanism.
In order to ensure uninterrupted operations, we conduct drills for abnormal system operations, cyber attacks, virus infections, data center fires, and other information security incidents, aiming to minimize losses caused by accidents.
We are audited annually by our customers, internal auditors and external third parties on information security.
In accordance with information security framework and control items of ISO 27001, the inspection is conducted with a total of 14 control categories.
Information Security Awareness Training and Promotion
Inventec leverages multiple channels to enhance employees’ information security awareness. In addition to publishing the latest intelligence of information security threats monthly, the Company posts information security articles in key areas of its facilities and displays employee information security guidelines on digital signage walls, fostering a corporate culture of shared responsibility for safeguarding information security. Information security training is tailored for different employee groups, including new hires, general staff, and technical professionals. Customized courses are provided accordingly, and social engineering drills are conducted to test employee awareness. In 2024, a total of 22 social engineering drills were conducted, with 44,824 emails sent out. The pass rate for the tests was 96.38%.
External Validation
In 2024, Inventec underwent 51 external inspections conducted by customers and independent third-party organizations to validate the effectiveness of its information security management system. In addition to preparing for certification under the updated ISO 27001:2022 standard, Inventec achieved government-issued Authorized Economic Operator (AEO) certification and received the TCSA Information Security Leadership Award for its information security governance. These achievements underscore Inventec's dedication to rigorous information security management. Furthermore, leveraging a third-party information security platforms to monitor key threat indicators, our external security posture assessment improved from a 'B' to an 'A' rating in 2024. Inventec remains steadfast in its commitment to the continuous enhancement of its information security capabilities. Currently, we have obtained ISO 27001 International Information Security Management Standard Certificates for our headquarters in Shilin, Taoyuan factory, Shanghai Pudong factory, Chongqing factory, Czech factory, and Mexico factory. For more details, please refer to Certifications and Certificates.
Information Security Incident Reporting Flowchart
.png)
Information Security Incidents
Item | 2021 | 2022 | 2023 | 2024 |
|---|---|---|---|---|
| Infringement of customer privacy or loss of customer information (number of cases) | 0 | 0 | 0 | 0 |
| Significant information security incidents and losses (amount) | 0 | 0 | 0 | 0 |

